Arti Karahoda
Cyber Security & Data Protection
Blog Feed
1. Technical Articles
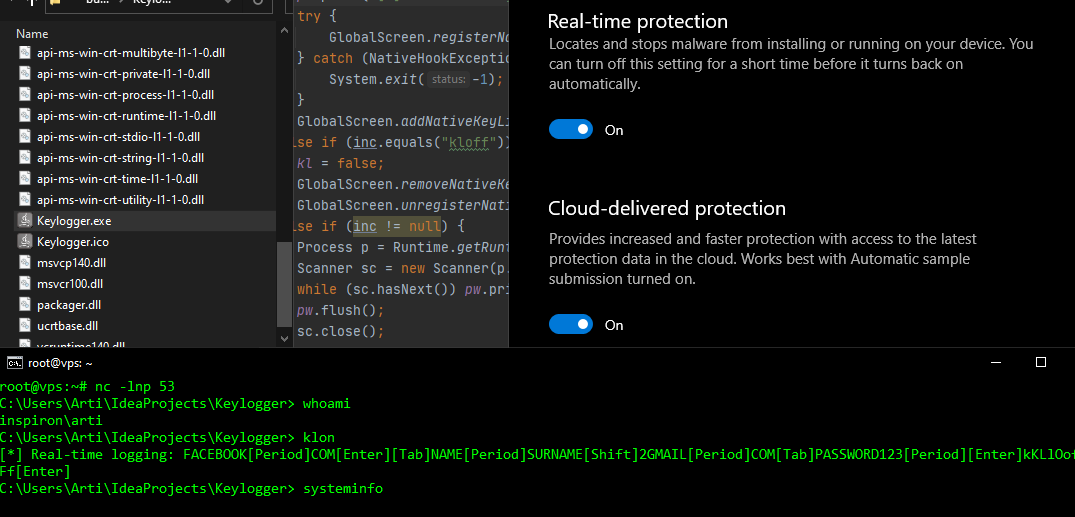 Evading AV with Network Sockets / Keylogger RAT
Evading AV with Network Sockets / Keylogger RAT
August 31, 2020 — Compiling and running an unsigned Windows executable and expecting a remote CMD session without any detection is a difficult task to achieve, however, sometimes there are easier ways of bypassing AVs. This article will outline a simple but functional remote ‘shell’ with keylogging capabilities against a fully up-to-date Windows Defender.
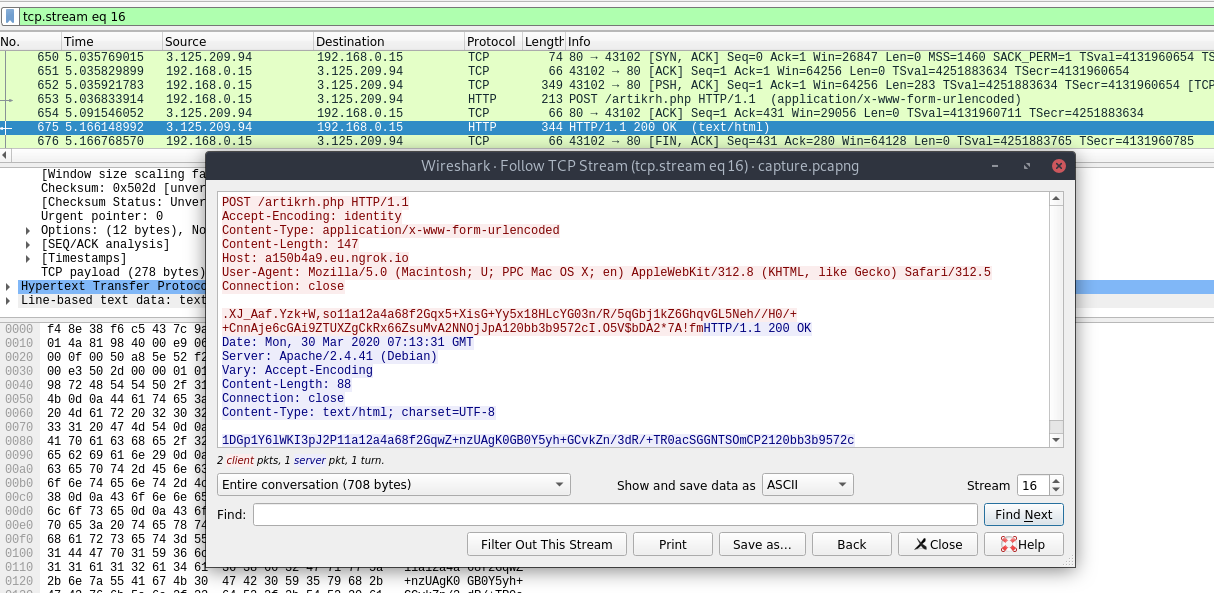 Weevely Backdoor Analysis / Blue Team DFIR
Weevely Backdoor Analysis / Blue Team DFIR
March 30, 2020 — Weevely is a powerful polymorphic backdoor used in web post-explotation; this tool is written in Python and it generates a small obfuscated PHP shell which is then delievered to the targeted web server. The article will lay out it’s communication chain and encryption scheme in order to assist blue team operators during a DFIR process.
 Building Android Spyware / Xombie APK
Building Android Spyware / Xombie APK
December 26, 2019 — Xombie APK is an Android spyware which works with the latest SDK version (API level 29). This research post will outline some functionalities that can be used for such purposes and for educational use only. The application is part of a larger project—SMS Xombie—which makes use of the GSM network to command and control infected devices.
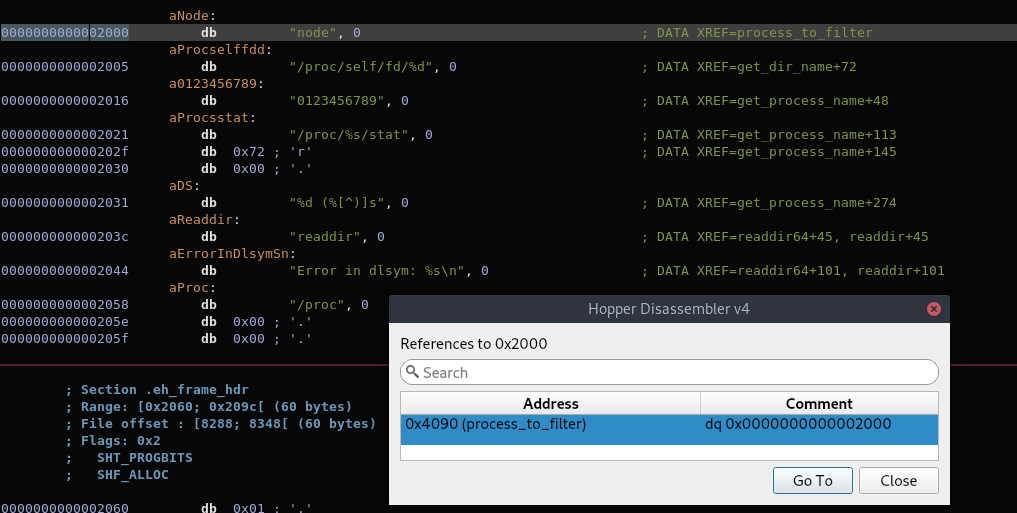 Ethereum RPC & IPFS / HTB Chainsaw
Ethereum RPC & IPFS / HTB Chainsaw
November 23, 2019 — This article will demonstrate a new vector of attack using Blockchain tools, commencing from an initial CMD injection through Ethereum’s RPC interface, SSH keys retrieval using the IPFS protocol, privilege escalation by stealing funds from a smart contract, and file system forensics in the slack space storage.
2. Sense Cyber Research Center
Cybersecurity Awareness Month #BeCyberSmart
October 31, 2020 —
This article is part of #NCSAM20 to help protect entities from online fraud and malware. It outlines key cyber-threats and their respective counter-measures in terms of safety tips – relevant to both individuals and businesses during the COVID-19 era.
A Look Inside Banka Ekonomike’s Data Breach
May 1, 2020 —
A comprehensive overview of the data breach incident at Banka Ekonomike in Kosovo by the DoppelPaymer ransomware. What information has been compromised, who is the entity behind the cyber-attack, and what are the key corporate security lessons?
Data Protection in Kosovo
August 1, 2019 —
A general outline on how Privacy & Data Protection are defined in Kosovo as well as data protection legislation throughout the years, key legal points, and the supervistory authority along its top court cases.
3. Capture the Flag Documentations
- September 30, 2018 — Access / MDB SQL & Stored Credentials
- August 28, 2018 — SecNotes / SQLi & Password Leak
- August 26, 2018 — Dab / Memcached Breach & Shared Library Hijack
- August 8, 2018 — Reddish / Node-RED, Pivoting & Rsync Abuse
- August 7, 2018 — Waldo / Local File Inclusion & Linux Capabilities
- July 19, 2018 — Hawk / AES CBC Bruteforce, Drupal Reverse Shell & H2 Console
- June 12, 2018 — Stratosphere / Apache Struts Attack & Python Library Hijack
- June 5, 2018 — Chatterbox / Achat Buffer Overflow & ACL Modification
- June 2, 2018 — Celestial / NodeJS Vulnerability & Cronjob Abuse
- June 1, 2018 — Poison / Exposed SSH key & VNC Takeover
$ whoami

About me: I am a Cybersecurity Specialist—from Prishtina, Kosovo—working in the field of Information Security and Data Protection. I completed my studies in Computer Engineering, Computer Networks, and Cyber Security. My key technical skills lie in enterprise security, network and mobile security, digital forensics, malware development and process automation using Python & C/C++.
Capture the Flag: I occasionally partake in CTF global events with a main focus on web, cryptography and steganography.
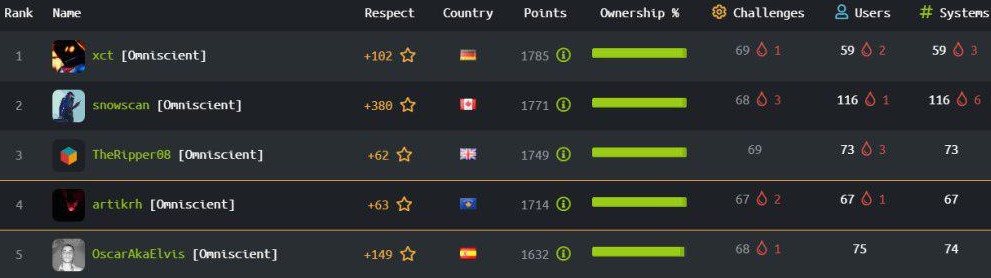
Hack the Box: HTB is an online penetration testing platform with more than 400,000 Security Researchers worldwide. My peak rank was the fourth (4th) position globally as seen below.
Team: Cyclone (Best rank: #2 out of 1931)
Mentions
- University of Business and Technology / CSP Academy 2021
- University of Prishtina / Cyber Security Presentation
- University of Prishtina / BSc. Diploma Thesis
- University of Business and Technology / CSP Academy 2020
- ICTSmedia / Albanian ICT Awards VIII
- Wallencore / XOR Regional CTF
- Cacttus Education / Cyber Security Panel
- Cyber Academy / Hall of Fame
- Sentry Cybersecurity / Cyber Defense Week
Links
- hackthebox.eu/profile/41600
- github.com/artikrh
- linkedin.com/in/artikarahoda/
- sense.co.com/cpo_team/arti-karahoda/